Private Registry - AWS ECR
Create Repositories
Before pushing images from an airgap bundle to a private registry create repositories for the following images:
Use a namespace of credoai when creating the registries for organization. The namespace will be used when configuring image pushes and private registry sourcing and avoids collision with other applications. It can also help support scoping registry privileges.
credoai/dexcredoai/mccredoai/miniocredoai/replicated-sdkcredoai/servercredoai/ui
Push Images
Use the kots cli to push images from the airgap bundle to the registry noted above.
You can use the AWS user access credential keypair directly to push images or have the aws cli handle them with AWS and aws ecr get-login-password for dynamic credentials.
Include the registry namespace after the hostname to ensure images are pushed the repos you created above.
# using aws cli for credentials
kubectl kots admin-console push-images \
./bundle.airgap \
123456789012.dkr.ecr.us-east-2.amazonaws.com/credoai \
--registry-username AWS \
--registry-password $(aws ecr get-login-password)
Kotsadm Registry Configuration
Navigate to the Registry tab in the kots admin console.
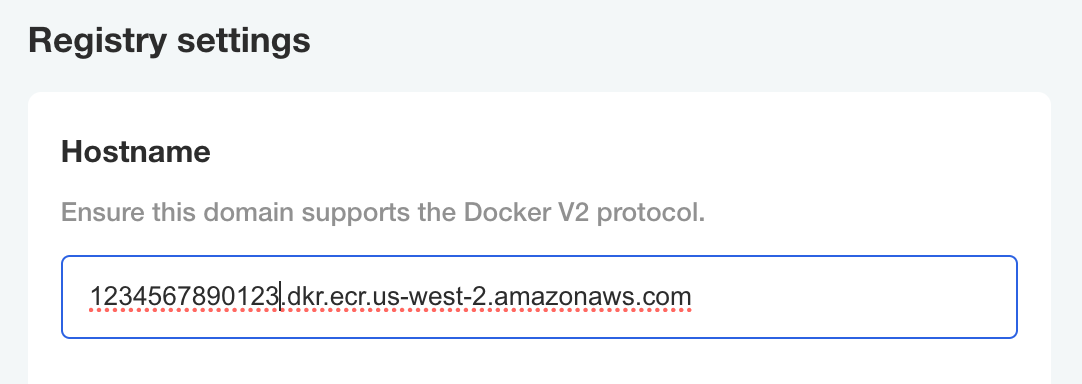
Registry Hostname and Namespace
Make sure the hostname matches the base hostname of the ECR registry you pushed images to excluding any namespace suffix.
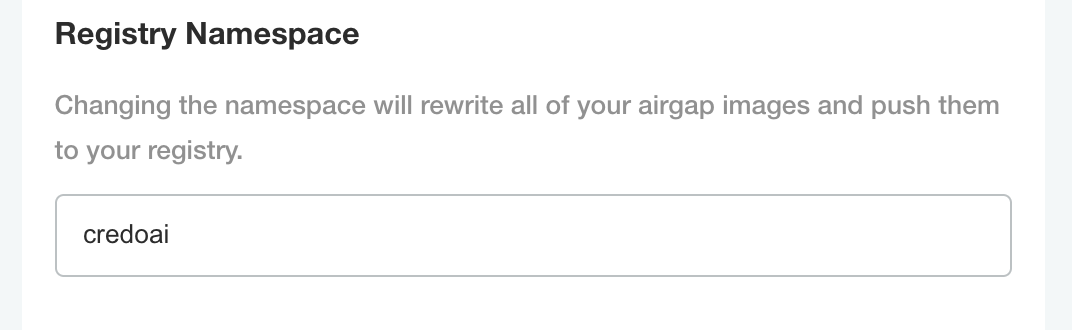
Use the Registry Namespace to set the namespace.
The credentials in this setup are primarily used to populate an imagePullSecret with basic auth for the configured registry. If you grant image pull privileges to your cluster nodes via another mechanism, these credentials and the IAM user are not required.
IAM User
Create an IAM user with ECR pull privileges. The reference IAM policy document below can be used to grant read-only permission to the ECR registry repositories.
{
"Statement": [
{
"Sid": "Auth",
"Action": ["ecr:GetAuthorizationToken"],
"Effect": "Allow",
"Resource": "*"
},
{
"Sid": "ReadOnly",
"Action": [
"ecr:BatchCheckLayerAvailability",
"ecr:GetDownloadUrlForLayer",
"ecr:GetRepositoryPolicy",
"ecr:DescribeRepositories",
"ecr:ListImages",
"ecr:DescribeImages",
"ecr:BatchGetImage"
],
"Effect": "Allow",
"Resource": ["arn:aws:ecr:us-east-2:123456789012:repository/credoai/*"]
}
],
"Version": "2012-10-17"
}
Generate security credential keypair and set these under the username and password.
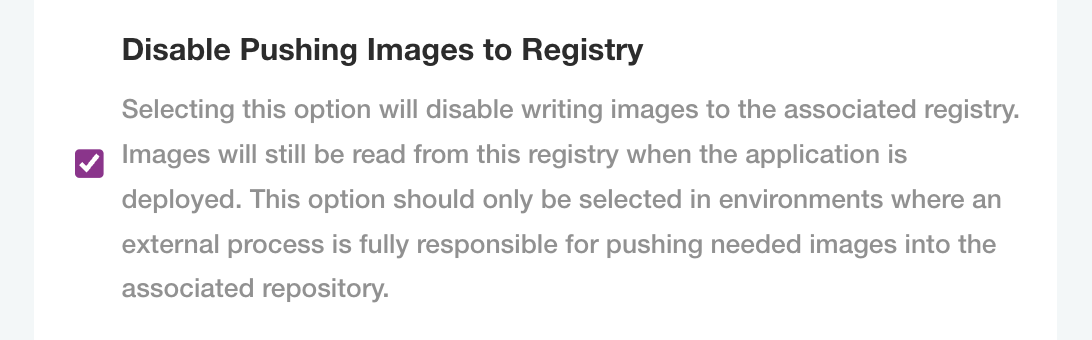
If you prefer to push images to the private registry via the kots cli, select Disable Pushing Images to Registry.
Other Auth Mechanism
If you are not using an IAM user, enter AWS as the username (the password can be blank).
Select Disable Pushing Images to Registry.

Save and Review
Click Save changes and go back to the Dashboard to review your registry changes in the diffs.