Vendor Portal
Prerequisites
- A hostname to be used for the vendor portal.
- An ingress controller that supports TLS termination.
- (Optional) A TLS certificate for the hostname.
Enable the Vendor Portal
-
Check the box "Deploy Vendor Portal"
-
Set the Vendor Portal Hostname
This is required to configure the platform to create the links provided in notification emails. It is also used when creating the ingress resource if k8s Ingress is used.
Configure the Ingress Resource
You can configure the ingress resource using the k8s Ingress option or by manually creating the resource.
k8s Ingress
-
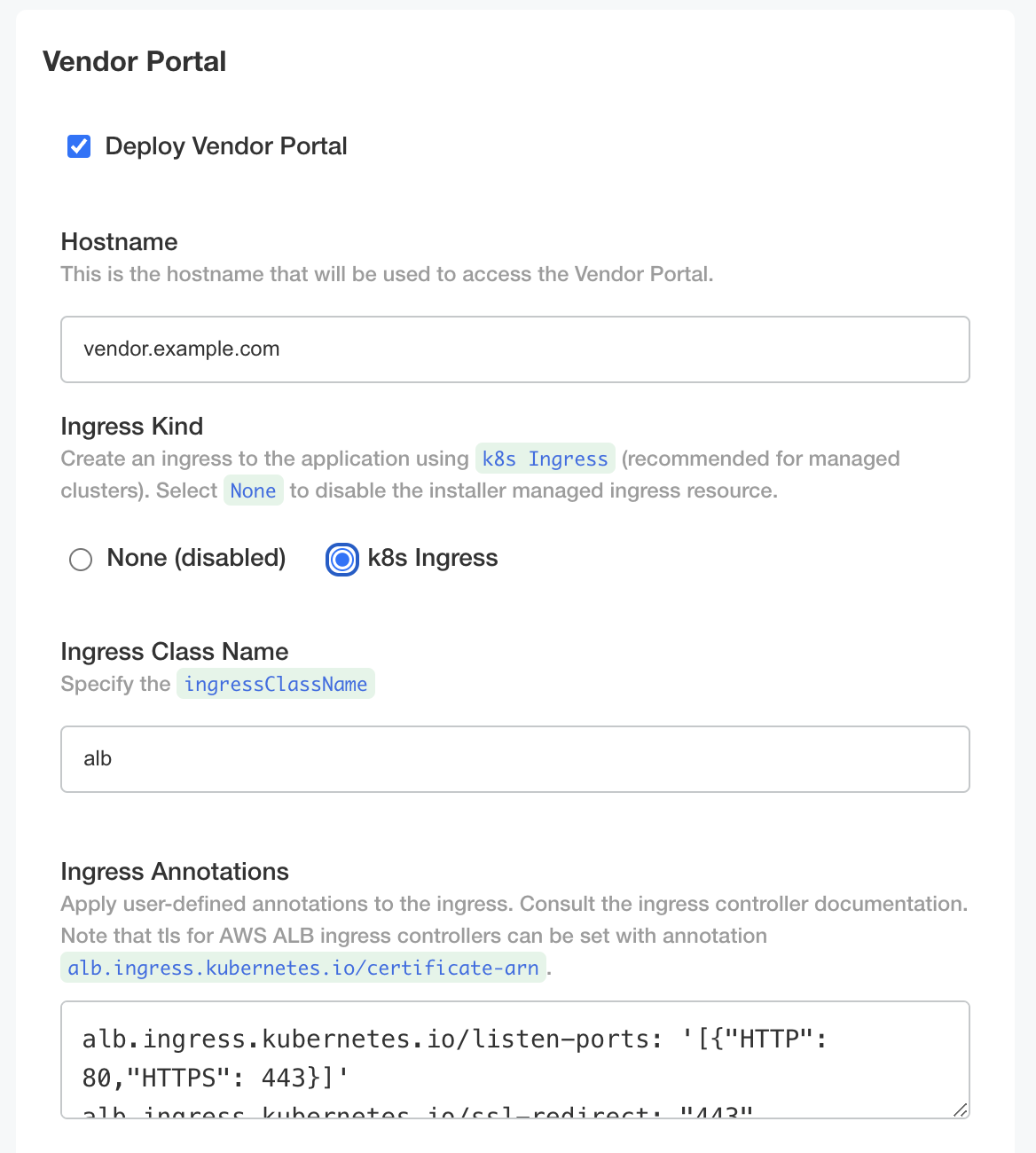
Select k8s Ingress
-
Set the Ingress Class Name
The following annotations are recommended when configuring the
albIngress Class.
alb.ingress.kubernetes.io/listen-ports: '[{"HTTP": 80,"HTTPS": 443}]'
alb.ingress.kubernetes.io/ssl-redirect: "443"
alb.ingress.kubernetes.io/target-type: ip
alb.ingress.kubernetes.io/scheme: internet-facing
Manual Ingress
-
Select None (disabled)
Be sure to set up your own ingress controller and configure the TLS certificate using the hostname you set in the previous step.
Example for httpproxy.projectcontour.io
With your TLS certificate and key in place, create the secret and HTTPProxy resource. In this example, the TLS files are named server.crt and server-key.pem.
NAMESPACE=credoai
VENDOR_PORTAL_HOSTNAME=<vendor-portal-hostname>
kubectl create secret tls credoai-vendor-portal-tls --cert server.crt --key server-key.pem
cat <<EOF | kubectl apply -n $NAMESPACE -f -
apiVersion: projectcontour.io/v1
kind: HTTPProxy
metadata:
name: credoai-vendor-portal
spec:
routes:
- conditions:
- prefix: /
services:
- name: credoai-vendor-portal
port: 4300
virtualhost:
fqdn: $VENDOR_PORTAL_HOSTNAME
tls:
secretName: credoai-vendor-portal-tls
EOF
Validate
kubectl get httpproxy credoai-vendor-portal -n $NAMESPACE
It should look similar to this:
NAME FQDN TLS SECRET STATUS STATUS DESCRIPTION
credoai-vendor-portal vendor.example.com credoai-vendor-portal-tls valid Valid HTTPProxy